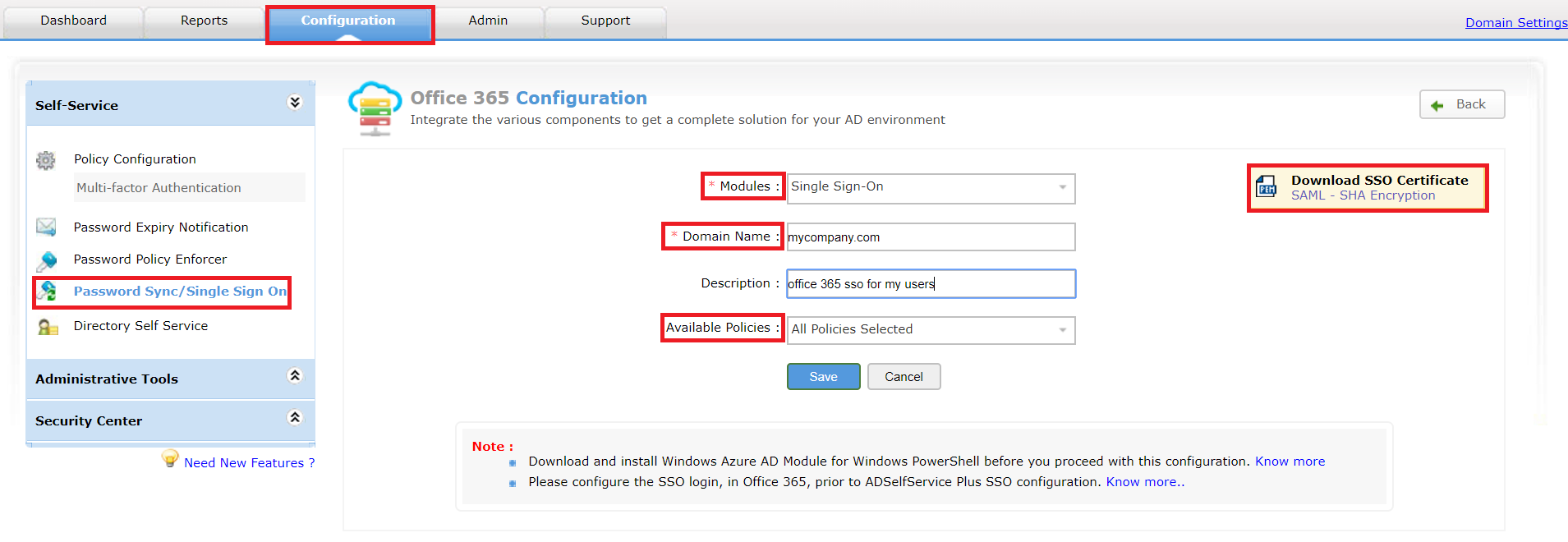
These steps will guide you through setting up the single sign-on functionality between ADSelfService Plus and Office 365.
-
Open Powershell with Admin rights.
-
Enter the below command. In the pop-up that appears, enter username and password of your Office 365 administrator account.
$cred = Get-Credential
-
Connect with MsolService using the following command.
Connect-MsolService -Credential $cred
Get-MsolDomain
This command will show a list of domains.
Note:
-
SSO can be enable only for domains that have the Status as Verified.
-
SSO can be enabled only for non-admin domains (domains that doesn't have onmicrosoft.com subdomain).
-
Enter the domain for which you would like to enable SSO.
$dom = "mycompany.com"
-
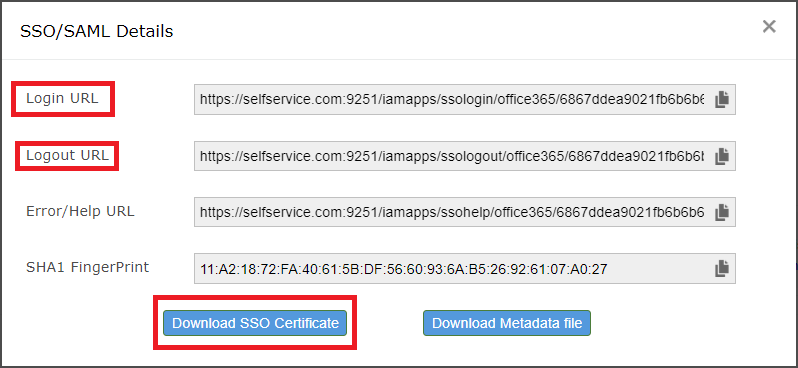
Enter the Login URL value from Step 5 of Prerequisite for $url and $uri commands, and Logout URL value for $logouturl command.
$url = "<login URL value>"
For example, $url = "https://selfservice.com:9251/iamapps/ssologin/office365/1352163ea82348a5152487b2eb05c5adeb4aaf73"
$uri = "<login URL value>"
For example, $uri = "https://selfservice.com:9251/iamapps/ssologin/office365/1352163ea82348a5152487b2eb05c5adeb4aaf73"
$logouturl = "<logout URL value>"
For example, $logouturl = "https://selfservice.com:9251/iamapps/ssologout/office365/1352163ea82348a5152487b2eb05c5adeb4aaf73"
-
Now copy the SSO Certificate file content (from Step 5 of Prerequisite) and past it as the value fo the below command.
Important: Please edit the file so that there aren't any new line before you copy the content.
$cert = "MIICqjCCAhOgAwIBAgIJAN..........dTOjFfqqA="
-
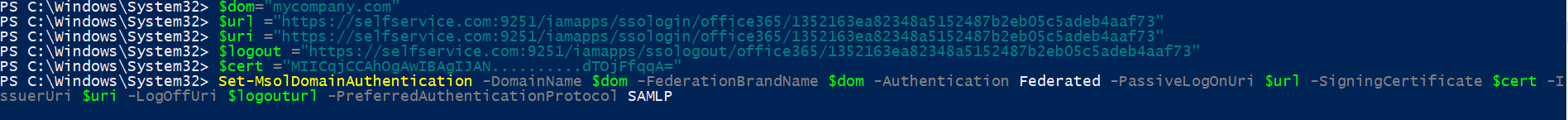
Run the below command to enable SSO in Office 365.
Set-MsolDomainAuthentication -DomainName $dom -FederationBrandName $dom -Authentication Federated -PassiveLogOnUri $url -SigningCertificate $cert -IssuerUri $uri -LogOffUri $logouturl -PreferredAuthenticationProtocol SAMLP
-
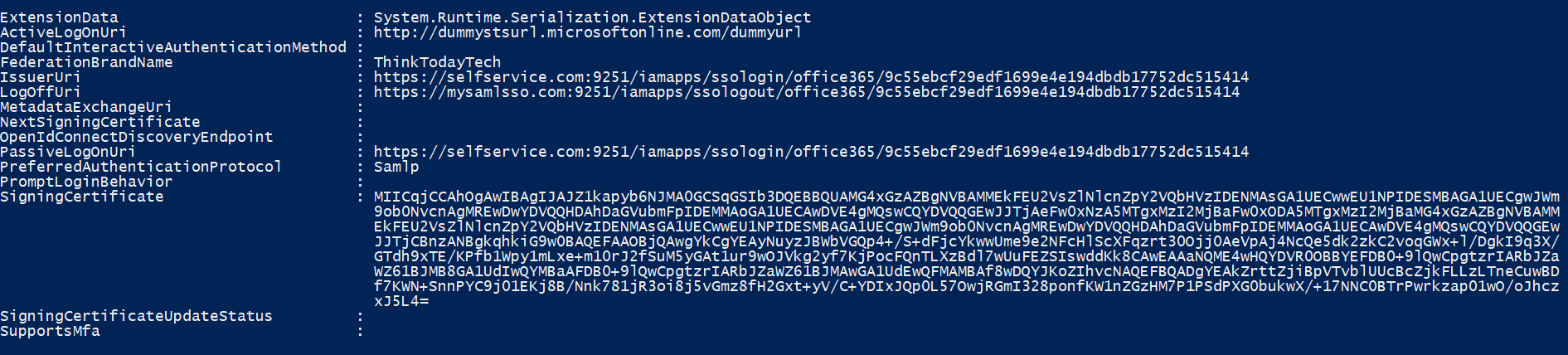
To test the configuration, use the following command.
Get-MSolDomainFederationSettings -DomainName "mycompany.com" | Format-List *
-
Reconfigure or update SSO settings: If you are already using SSO for Office 365 from another identity provider or want to update ADSelfService Plus SSO settings, then you must first disable SSO in Office 365, and then follow the steps in this guide. To disable SSO in Office 365, use the command given below:
$dom = "mycompany.com"
Set-MsolDomainAuthentication -DomainName $dom -FederationBrandName $dom -Authentication Managed